NSO Group’s software can record your calls, copy and secretly record your messages
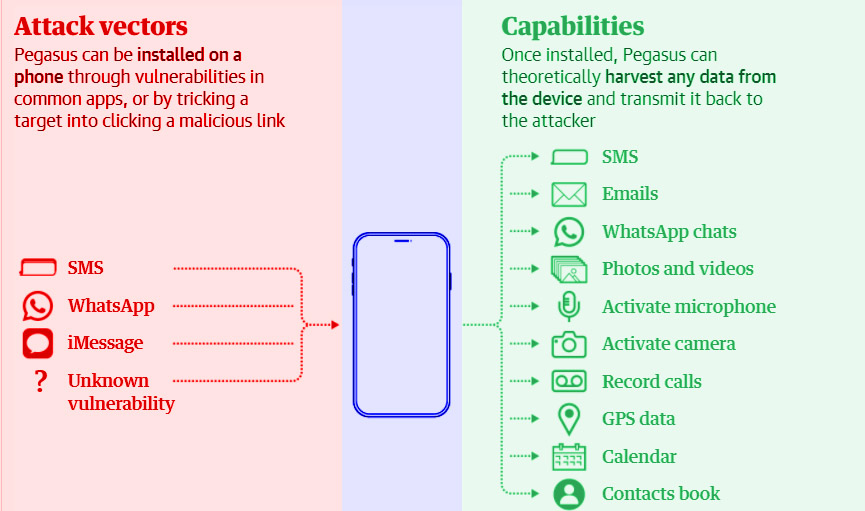
It is the name of perhaps the most influential spyware ever developed, indeed by a private company. Once it reaches your phone, you can turn it into a 24-hour surveillance device unnoticed. You can secretly record it through your phone’s camera or activate the microphone to record your conversations. You can copy the messages sent or received, collect your photos, and record your calls. They may be able to point out where you are, where you’ve been, and who you’ve met.
Pegasus is pirated software (or spyware) that the Israeli company NSO Group develops, markets, and licenses to governments worldwide. It can infect billions of phones running iOS or Android operating systems.
The first version of Pegasus, discovered by researchers in 2016, infected phones through what is known as spear phishing: text messages or emails that trick a target into clicking on a malicious link.
Table of Contents
What’s In The Data Leak?
The data inaugural is a list of more than 50,000 phone figures selected as of anxiety since 2016 by government customers of the NSO Group, which sells surveillance software. The data also includes the time and date the numbers were selected or entered into a system. Forbidden Stories, a Paris-based not-for-profit journalistic organization, and Amnesty International initially had access to the list and shared access with 16 media organizations, including The Guardian. More than 80 journalists worked together on the Pegasus project for several months. Amnesty’s security laboratory, the project’s technical partner, carried out the forensic analyzes.
What Does The Leak Indicate?
The group believes the data indicates potential targets that NSO’s administration customers identified before possible shadowing. Although the data indicates intent, the presence of a number in the data does not mean whether an attempt was made to infect the phone with spyware such as Pegasus, the company’s signature monitoring tool. Success. The presence of a tiny quantity of US landlines and numbers in the data that NSO’s tools describe as “technically impossible” indicates that some destinations were selected by NSO customers when they were not. . they could infected with Pegasus. Though, forensic examinations of a small sample of cell phones with numbered numbers found close correlations between the time and date of a number in the data and the start of Pegasus activity, in some cases just seconds.
What Did The Forensic Analysis Show?
Amnesty has investigated 67 smartphones that suspected of being attacked. Of these, 23 were successfully infected, and 14 showed signs of attempted penetration. The remaining 30 tests were unsuccessful in several cases because the phones were replaced. Fifteen of the phones were Android devices, none of which presented signs of successful infection. However, unlike iPhones, Android phones do not record the type of information that Amnesty’s detective work requires. Three Android phones presented signs of targeting, such as the SMS messages associated with Pegasus.
Which NSO Customers Dialed Numbers?
Although the data organized into groups that point to individual NSO customers, it does not tell which NSO customer was responsible for selecting a particular number. NSO claims to sell its gears to 60 customers in 40 countries but refuses to identify them. By carefully examining the targeting pattern of individual customers in the leaked data, the media partners could locate ten governments believed to responsible for target audience selection: Azerbaijan, Bahrain, Kazakhstan, Mexico, Morocco, Rwanda, Saudi Arabia, Hungary, India. and the United Arab Emirates
What Does The NSO Group Say?
You can read the complete statement of the NSO Group here. NSO said the consortium made “wrong assumptions” about which clients using the company’s technology through its attorneys. The 50,000 figure was “exaggerated,” and the list could not a list of numbers “targeted by governments with Pegasus.” The attorneys said the NSO had reason to believe that the list accessed by the consortium “is not a list of government-designated numbers with Pegasus, but could part of a larger list of numbers.”
“That the goal.” NSO Group customers may have used it for other purposes. “After further questioning, the attorneys said the consortium based its findings” on a misleading interpretation of leaked data from accessible and available basic information, such as HLR Search Services, that did not affect the target list of clients of Pegasus or others. “Products … we still don’t see any connection among these lists and nothing related to the use of the NSO group’s skill.
What Is HLR Lookup Data?
The term HLR or Home Location Register describes a database that is essential for the operation of cellular networks. Such logs keep records of phone users’ networks and their general locations and other identifying information commonly used to route calls and text messages. Telecommunications and surveillance experts say that HLR data can sometimes be used in the early stages of a surveillance attempt to determine if a phone can be connected. The consortium knows that NSO customers can search for HLRs through an interface on the Pegasus system. It is not clear whether Pegasus operators need to perform HRL searches through their user interface to use their software; an NSO source emphasized that regardless of Pegasus, their customers could have various reasons for conducting HLR searches through an NSO system.
Since then, however, NSO’s attack capabilities have evolved. Pegasus infections can be reached through so-called “zero clicks” attacks, which do not require any interaction from the phone owner to be successful. These often take advantage of “zero days” weaknesses, that is, bugs or errors in an operating system that are not yet known to the mobile phone manufacturer and therefore could not be remedied.
In 2019, WhatsApp announced that the NSO package had been used to deliver malware to more than 1,400 phones by exploiting a zero-day susceptibility. More lately, NSO has begun exploiting weaknesses in Apple’s iMessage software, granting it backdoor access to hundreds of millions of iPhones. Simply making a WhatsApp call to a target device could install malicious Pegasus code on the phone even if the target never replied to the call. Apple says it constantly updates its software to prevent these types of attacks.
HLR
The technical understanding of Pegasus and how to find the conclusive breadcrumbs it leaves on a phone after a successful infection has been enhanced thanks to research by Claudio Guarnieri, director of Amnesty International’s security laboratory in Berlin.
“It’s increasingly difficult for targets to understand,” said Guarnieri, who found that NSO customers had largely abandoned suspicious SMS messages for more subtle, clickless attacks.
Companies like NSO find it particularly attractive to leverage software that comes by default on devices like iMessage or widely installed devices like WhatsApp, as it dramatically increases the number of cell phones that Pegasus can positively attack.
As a technical partner for Project Pegasus, an international consortium of media organizations including The Guardian, Amnesty Lab has discovered traces of successful attacks by Pegasus clients on iPhones running the latest versions of Apple’s iOS. The attacks only took place in July 2021.
Forensic analysis of victims’ phones also found evidence that NSO’s constant search for vulnerabilities may have spread to other popular apps. In some cases that Guarnieri and his team analyzed, strange network traffic related to Apple’s Photos and Music apps can be seen at the time of infections, suggesting that NSO may have started manufacturing new Sch files. Send
How Pegasus Infiltrates A Phone And What It Can Do
“When an iPhone cooperates, it done in a way that allows the assailant to gain so-called root or manager rights on the device,” said Guarnieri. “Pegasus can do more than the owner of the device.”
NSO lawyers alleged that Amnesty International’s technical report was a guess and called it “a compilation of speculative and unsubstantiated assumptions.” However, they did not question any of their specific findings or conclusions.
NSO went to great lengths to make their software more difficult to detect, and Pegasus infections are now complicated to identify. Security researchers suspect that newer versions of Pegasus only use the phone’s temporary storage and not the hard drive, so virtually all traces of the software disappear when the phone is turned off.
One of Pegasus’s most significant challenges for journalists and human rights defenders is that the software exploits undetected vulnerabilities so that even the most security-conscious cell phone user cannot prevent an attack.
“I get this question almost every time we do a forensic analysis of someone: ‘What can I do to prevent this from happening again?” “said Guarnieri.” The truthful answer is nothing.
The technological advances of this century have fueled social movements and democratized access to information in India and worldwide. This is a value we take seriously at The Guardian, which is why we don’t install a paywall and instead keep our independent journalism open and free. But the same skill has also been used by those in power to seize our personal information, manipulate our behavior, and turn away from the police.
Infiltrates
From the Snowden revelations to the Cambridge Analytica scandal to our constant scrutiny of great technology, The Guardian has a long history of exposing how technology can abuse democracy and human rights. If you appreciate this mission, join us today. Your support will enable our investigative journalists to question further the governments and giant profit machines of Silicon Valley. People should control the technology, not the other way around.
With no billionaire shareholders or owners, we can set our schedule and deliver reliable journalism that is free from commercial and political influence and counteracts the spread of misinformation. If it has never been more critical, we can examine and challenge without fear or favor.
Unlike many others, Protector reporting is available to everyone regardless of what they can afford. We do this because we trust in the same information.
Ten million people have trusted The Guardian’s influential journalism since our publication 200 years ago and turn to us in times of crisis, doubt, solidarity, and hope. More than 1.5 million booklovers from 180 countries have recently supported us financially and made us open and highly independent.
More Inside Techinfofdy.com
What is Ransomware? How Ransomware Works?
5 Best Enterprise Password Management Software